We are now seeing an increase in the reporting of cyber crime, data breaches and ransomware attacks, these are some of the high profile incidents that have occurred in the UK :-
September 2018
British Airways is hacked with 380,000 bank card details compromised

British Airways has been hit by a hack attack that has compromised customers bank card information that took place between the 21st August and 5th September . The airline has made a pledge to compensate any customers that have suffered financial loss as a result of this data breach.
It is understood that the National Cyber Crime Agency and the National Cyber Security Centre have been advised . The ICO have also been formally advised due to the data breach and to comply with the recent GDPR regulations.
The type of information stolen is customers names, e-mail addresses , home addresses and payment card details.
Details of how the actual breach took place are still awaited .
June 2018
Dixons Carphone Suffers Massive Data Breach

Dixons Carphone have suffered a huge data breach which is thought to have involved 5.9 million payment cards and 1.2 million customers personal data which apparently occurred over a year ago.
The firm has stated that it is unaware of any of customers details having been used to carry out fraudulent transactions but attempts have been made to use 105,000 cards that do not have chip and pin protections via one of the processing systems of Currys PC World and Dixons Travel stores.
This cyber attack has impacted on the Dixons Carphone shares with 3% of their value being lost.
The incident has been reported to the ICO and GCHQ are helping with the investigation.
Under the new GDPR data protection regulations businesses can be fined up to 4% of their global annual turnover but as this breached occurred prior to this the maximum fine that could be levied would be only £500,000.
September 2017
UK National Lottery hit by offline DDoS Attack

Thousands of on-line customers were unable to access the Lottery via their smart phone app in order to gain access to the website and purchase a ticket. This was caused by an outage that produced a DDoS attack , it is unsure as to who was behind the DDoS attack and it does appear to be an isolated attack with no other gambling sites being affected.
The attack took place for about 90 minutes on 3oth September between 6pm and 7.30pm which is one of the peak times for tickets being purchased.
The National Lottery has recently been subject to e-mails threatening that a DDoS attack would be carried out unless a bitcoin ransom was paid.
June 2017
Global Ransomware Attack Hits Businesses Again
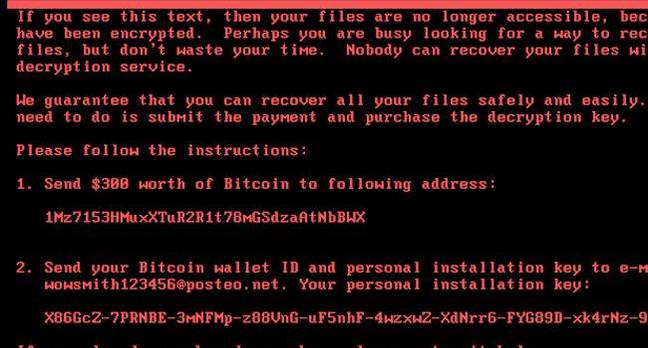
A global ransomware attack attack has hit businsess throughout the world. The malware attack is a version of the Petya ransomware which is being named “Golden Eye” or “Not Petya ” The ransomware attack has so far infected 2,000 machines affecting the Danish shipping firm Maersk , US pharmaceutical business Merck , the advertising business WPP and the law firm DLA Piper. Most hard hit were it is believe are the countries of Russia and the Ukriane.
This form of ransomware appears more dangerous that the recent WannaCry strain which is still very much active.
It is again only affecting windows operating systems with two main threat vectors , a phishing e-mail and via an accounting software update from MeDoc. the malware relates to the leaked Eternal Blue SMB exploit which steals credentials to instruct other personal computers to run the malware. There is also no “kill” switch unlike WannaCry.
Ransomware Attack Hits Leading London University
University College London (UCL) has been hit by a ransomware attack which has caused significant disruption.
The attack was initially thought to be as a result of a phishing e-mail but it is now perceived to emanate from contact with a compromised website when a user clicks on a pop-up page that can then spread the malware.
It is understood that the attack has now been contained but the university have issued a warning that students need to be wary of any suspicious attachments sent via e-mail.
UCL immediately switched all drives to “read only” which prevented the malware from carrying out substantial damage.
The attack seems to be aimed at disturbing the students that are currently studying for exams rather than the compromising of research information.
The perpetrators behind the attack are yet unknown.
May 2017
NHS Hit By Massive Cyber Attack
NHS services across England and Wales were hit by a massive cyber attack whereby staff could not access patients data as it has been scrambled by a ransomware attack.
It is understood that 39 NHS organisations and some GP practices have been impacted by this cyber attack. Operations director appointments were cancelled.
The National Security Centre (NCSC) is working with the NHS to ascertain who is behind this attack. At the moment there appears to that no patient data has been stolen.
NHS Digital have issued a statement that the ransomware attack was not specifically targeted at them and it does seem that this is part of a more widespread cyber attack around other parts of the world that is believed to have affected 75 countries. This includes the USA, Russia and Spain.
The attack was caused by the malware know as Wanna Decryptor.
It is likely that the ICO will launch an investigation into this cyber attack in view of the scope and impact that this has had on the NHS.
Update
To date 200,000 users have been affected by the ransomware attack and approximately £40,000 has been taken in bitcoins. This however has only been collected by a very limited of bitcoin pockets which suggests that this was perhaps not intended to be a significant attack and one that might have just got out of hand.
Debenhams Florist Website Suffers Cyber Attack
The florist website of Debenhams has been hit by a cyber attack where 26,000 customers may have had their personal data compromised.
The information stolen includes names and addresses which were accessed via a third party e-commerce website called Ecomnova .
It is understood that Debenhams have contacted all the users by e-mail and followed up with a subsequent e-mail that had their data compromised.
The cyber attack took place between the 24th February and 11th April with the website still remaining off-line. The precise nature of the attack has not been released .
A full investigation is under way , the ICO have also been advised of this incident.
November 2016
National Lottery accounts hacked

Hackers gained access to 26,500 National Lottery accounts with the use of passwords and e-mail addresses that had been stolen from previous breaches.
The attack was detected by Camelot who run the National Lottery and responded by locking down customers accounts which triggers compulsory password resets and contacting those customers who were affected by this attack. It is thought that only 50 accounts were subject to suspicious activity and that this was only related to the changing of personal details.
It is understood that Camelot are working with the National Crime Agency and the National Cyber Security Centre to assess the criminal actions that have taken place. The ICO are also carrying out an investigation.
This is another example that were individuals use the same passwords if fallen into the wrong hands these can be used to access other on-line accounts.
Three Mobile customer database compromised

Three Mobile have advised that a customer database has been compromised as a result of a hacker attack, it is understood that 133,827 customers may have suffered a data breach.
The hackers are understood to be two men from Kent and Manchester had managed to access data that consisted of names , addresses and dates of birth, this information was then used to purchase new phones that were eligible for a hardware upgrade. Three have said that only 8 phones were stolen.
David Dyson , the CEO has stated that no payment information or password data of their customers was taken an that all customers affected were contacted.
The UK’s National Crime Agency have arrested the two individuals and a third person.
The ICO have not made any public comment but it is assumed that an investigation into this breach of personal data with follow.
Tesco bank accounts hacked
40,000 customer accounts of Tesco bank out of a total of 136,000 were subject to suspicious transactions, 9,000 of these had money stolen from their accounts. The sums taken were relatively small varying up to amounts of £600 but eventually totaled £2,500,000.
It is understood that the bank was barring customers from making on-line payments using their debit card but this was only a temporary stance by the bank. Customers were however still able to use their cards to make cash withdrawals and chip and pin payments. No personal data of customers was been taken.
The bank has not released what has caused this incident , but have only stated that accounts “have been subject to on-line criminal activity”. It is interesting to note that no reference has been made to hackers which could suggest that it is thought that the compromise of the customer accounts were as a result of an insider.
Benny Higgins , the Chief Executive of Tesco’s bank has stated that all customers impacted by this will be refunded which we understand has now been carried out.
This incident is one of the biggest recorded banking security breaches so far in terms of number of customers affected.
The Financial Conduct Authority , the National Crime Agency and the Information Commissioners Office have all been notified and an investigation has begun. Depending on the outcome of this Tesco could be hit by a fine for failing to have appropriate security measures in place for safeguarding individuals personal data, should this be found to be the case.
It is feared that smaller banks could be a new target as they are perceived as being more vulnerable to possible attacks as they do not have significant cyber security budgets compared to the larger banks.
So far this year the increase in attacks on financial institutions has reached 75 , compared to to just five only two years ago.
October 2016
Hospitals in Lincolnshire hit by computer virus

Hospitals in Grimsby , Scunthorpe and Goole , Boston and Lincoln have been subject to a cyber attack after an NHS computer network was compromised.
This occurred on the 30th October and has been classified as a major incident by the Northern Lincolnshire and Goole NHS Foundation Trust (NLAG).
As a result of this operations were cancelled as computer systems had to shut down in order to contain the cyber attack.It is thought that operations would be not be undertaken for 5 days until it was ascertained that the systems had been fully restored.
It is not yet know who was behind this attack
An incident response plan has been implemented to manage the disruption and delays caused to the hospitals.
August 2016
Sage Group Hit by Data Breach
Sage Group who provide accounting , payroll and payments software for many small and medium sized business have disclosed that an internal login has been utilized to gain unauthorized access to the data of of a number of its British clients.
It is understood that the personal details of the employees of about 280 British companies were possibly exposed in this breach, however it is has not yet been determined whether any data has been stolen but personal details and bank account information may have been compromised.
What it seems is certain is that an internal login has been used to access the data and a full investigation is under way. The City of London police have been notified of this incident.
Sage have also advised the Information Commissioners Office ( ISO) of the data breach who will no doubt require full details of how this breach occurred and what measures Sage have since implemented to prevent any further possible insider threats of this nature.
http://www.reuters.com/article/sage-group-cyber-idUSL8N1AV0JO
June 2016
Cheltenham Hairdressing Salon victim of ransomware attack
A local Cheltenham hairdresser discovered that their computers not longer worked which meant that they were unable to access their electronic diary to make and check bookings and to access their contact details.
The salon will need to pay the ransom in order to retrieve the stolen data taken by the hackers which originated from an Indian e-mail address.
The hackers demanded a ransom of £1,600 of bitcoins in return for the stolen data. The matter was reported to Gloucestershire police who requesting that they do not pay this, however it does seem likely that they will. The salon also estimates that it will loose circa £6,000 and £7,000 in loss of revenue from this ransomware attack.
The salon did have anti virus software installed on their computer system and had also arranged back of their data.
Ransomware attack on Gloucestershire hair salon
London Stock Exchange hacked by Anonymous

The London Stock Exchange was apparently taken down for two hours by the hacking group Anonymous .
Anonymous claimed the scalp of the London Stock Exchange as part of it’s on-going protest against the world’s banking sector.
It is understood that the attack took place at about 9am on the 2nd June . The attack is believed not to have affected trading and no sensitive data was accessed .
The London Stock Exchange has provided no formal comment on the incident.
May 2016
Mumsnet hacker attack was a teenager
The Mumsnet website was notoriously hacked twice last year in July and August and up until now it has not be possible to identify who was responsible.
The founder of Mumsnet ,Justine Roberts and one other user were targeted is swatting attacks which involved making an emergency call to police advising that a crime is taking place at the home of the intended victim in order to get the police to send a team to investigate at the home in question.
A distributed denial of service attack (DDOS) was also involved in an attempt to push the website offline by flooding it with internet traffic.
The parenting site had to reset its 7.7 million members’ passwords.
A teenager has now been charged with the hacking attack .
March 2016
NatWest accounts accessed by “SIM swap fraud”
NatWest bank were subject to a challenge to their security procedures after journalists from BBC Radio 4’s You and Yours program managed to access an account online taking money.
Bank customers accounts have been successfully attacked by criminals who divert mobile phone accounts whereby hackers persuade phone providers to divert mobile phone numbers. This scam is recognized as “SIM swap card fraud”.
On occasions banks text security details when customers forget their details with the activation codes sent by text to mobile phones allowing payments to be made from the account.
The scam works by blocking the genuine phone with the owner unaware as to why the phone has been blocked and allows the hacker ( who now has control of their phone) – to access funds from the bank account.
The real concern is that You and Yours managed to access the account online without knowing the customers number, PIN or any passwords, neither did they have any other confidential information such as mother’s maiden name, pet’s name or first school. The PIN was changed and password which enabled the account holder to be locked out of the bank account.
Only £1.50 was transferred, a token amount to demonstrate how this could be carried out.
NatWest have advised that its systems would changed as a result of this.
January 2016
Lincolnshire County Council Malware Attack
Lincolnshire County Council was been subject to a £1m ransomware demand which forced the council to shut down their PCs and servers across their entire network. It is understood that this was caused by an email containing malware that was launched by a member of staff following a phishing attack.
The malware encrypted a number of files before deleting itself and presenting a ransom demand of £1m in bitcoin, in return for the decryption keys.
The malware was new to the organisation’s security software provider who is now having to release signature files for its anti-virus and anti-malware software. It is believed that only one user was behind the ransomware attack .
The decision to shut down the entire network was made after that member of staff realized what had happened and contacted their IT team . Employees were also alerted by the sudden encryption of files on the network.
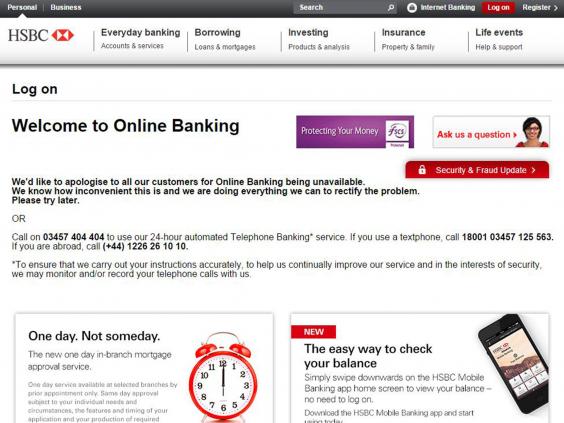
HSBC’s online banking website went down impacting on thousands of customers being unable to access their banking services after the cyber attack.
Anyone attempting to access their account would have received the following screen shot :-
The attack was a distributed denial of service (DDos) attack but the source was known. HSBC successfully defended their systems and no data was compromised during the attack
During the attack HSBC were directing customers to utilize the bank’s automated telephone banking services instead. It is possible that this day was targeted because for many people this was their first pay day after Christmas and that traffic on this day would have been higher than normal.
HSBC are currently working with the government -backed Computer Emergency Response Team , Cert -UK to try and ascertain who was behind the cyber attack.
Irish Government hit by Cyber Attacks
A number of the Irish Government’s websites were shut down for up to 12 hours by a distributed denial of service (DDoS) which targeted among others the Department of Justice, the Courts Service and the Oireachtas.
For some the disruption lasted one hour but other sites were shut overnight up. This attack follows the shut down of the lottery on Wednesday, operated by Premier Lotteries Ireland, with ticket sellers also taken offline as they prepared for one of the biggest draws of the year.
The DDoS type of cyber attack is not normally result in a data breach that leads to the theft of personal information but to prevent use of websites and services.
The driver of the hack attack is believed to stem from a video, purportedly from the group, Anonymous which was posted online over a year ago in whereby threats were made over the imposition of water charges.
Irish Government hit by Cyber Attack
Hackers target house conveyancing industry
It has been reported by the Daily Telegraph that in excess of £10 million has been stolen by hackers who have managed to gain access to the e-mails of individuals buying and selling houses.
Over 90 people have succumbed to this and it is understood that the average amount stolen is £112,000.
The hackers gain assess to e-mail chains between sellers and buyers, their solicitors and estate agents. The hackers then send an e-mail, normally on the day of completion advising the parties that the bank account details have changed at the last minute and that the funds should be deposited in another bank account.
The funds are then deposited into another bank account and then transferred electronically to bank accounts around the world where it becomes very difficult to track.
This is not a new activity by hackers. A couple sold their £340,000 flat last year whereby the funds were transferred by their solicitor into a hackers account. Again the e-mail chain was hacked and they sent an e-mail to the solicitor pretending to be the sellers requesting that the money was transferred into another account.
The National Fraud Intelligence Bureau, which operates the Action Fraud reporting hotline, recorded 91 conveyancing fraud crimes up to last October. In September and October alone, 16 cases were reported to Action Fraud, an average of two a week.
December 2015
BBC iPlayer compromised again
On New Years’ Eve this week the BBC iPlayer and some of the BBC webpages were hit by a distributed denial of service attack. Visitors to the BBC sites were welcomed with error messages and a number of programs that failed to load properly, while some visitors were locked out entirely.
The group claiming responsibility were the New World Hackers who claimed to want test their own capabilities. It is understood that the crash lasted for approximately 4 hours.
In a message sent to BBC technology correspondent Rory Cellan-Jones, which he later posted on Twitter, the group said: ‘It was only a test, we didn’t exactly plan to take it down for multiple hours. ‘We realize sometimes what we do is not always the right choice, but without cyber hackers … who is there to fight off online terrorists?’
BBC’s business correspondent Joe Lynam described it as ‘quite a serious claim to make’ although the BBC ‘cannot verify or prove their claims’.
This was not the first time that a cyber attack has caused the BBC’s sites to crash. In July 2014, iPlayer went offline for a weekend after a fault developed in the database of the on-demand TV service.
JD Weatherspoons’ suffer data breach
JD Weatherspoons, the high street pub chain , announced that that have suffered a data breach of 656,723 customers as a result of a hacker attack .The database consisted of personal details such as their names, dates of birth, email addresses and mobile phone numbers, no passwords were stolen.
The company has emailed customers and appointed a cybersecurity specialist to investigate the data breach. The Information Commissioners Office, which regulates data protection, has also been notified.
The card data was not encrypted because the first 12 digits and the security number on the back of the card were not stored on the database.
The data breach happened between 15 and 17 June. JD Wetherspoon said it had taken time to notify customers of this breach because the data was held by a third party company that previously hosted its website, and the breached had not been discovered until 1 December.
According to JD Wetherspoon chairman and founder Tim Martin, an anonymous email was sent alerting him to the attack on 6 November. This however went to company’s spam folder, the breach was not discovered until the company was contacted by the Financial Times on Monday.
October 2015
Talk Talk Hacked
The phone and broadband provider TalkTalk suffered a cyber-attack in which personal and banking details may have been accessed by hackers. It is understood that TalkTalk did not know how much of the customer information was encrypted.It said it would contact all its four million current customers and advised that an unknown number of previous customers may also be at risk.It was however ascertained later that only 157,000 customer may have been compromised.
TalkTalk said complete credit card details were not stored in its system and that account passwords were not accessed. They now expect the amount of financial information that may have been accessed to be materially lower than initially believed and would on its own not enable a criminal to take money from your account.
TalkTalk have hired defense company BAE Systems to investigate the hacking attack that may have led to the theft of the personal data.
It has recently been reported that a 15-year-old boy has subsequently been arrested in Northern Ireland in connection with the TalkTalk hacking attack.
It is understood that TalkTalk purchased an errors & omissions policy that included cyber coverage via insurer Zurich. The type of losses that may be covered under the policy could include Business Interruption , Crisis Management and Privacy Breach Costs.
The latest estimate of the cost of the data breach provided by TalkTalk is between £30M – £35M. The bulk of this loss is thought to be attributable to business interruption losses.
Speculation as to the cause of the data breach is via a SQL injection. This may have related to a vulnerability in the original software by the software provider.
Most recently , Codefield Security , a mobile cybersecurity testing firm , have discovered a series of vulnerabilities on TalkTalk’s website and e-mail services still remain which could lead to hackers being able to steal e-mail addresses , passwords and financial data.
As a result of the data breaches it is understood from market researchers, Kantar Worldpanel, that Talk Talk has lost almost 5% of its home customers market share
Vodafone Hacked
Vodafone says hackers have accessed the accounts of 1,827 customers, just a week after a separate hacking attack at TalkTalk.
The hack could potentially give criminals customers’ names, mobile numbers, bank sort codes and the last four digits of their bank accounts.
The company said an attempt had been made to access some of its customers’ account details between midnight Wednesday and midday on Thursday.
An investigation has been launched by the company and the National Crime Agency and communications watchdogs were told on Friday.
A Vodafone spokesman confirmed 1,827 customers had their accounts accessed but added that the information obtained by the hackers “cannot be used directly to access customers’ bank accounts”.
The information does leave the customers open to fraud and perhaps phishing attempts, however, and Vodafone said the banks of affected customers had been contacted.
Vodafone said it is also contacting affected customers and helping them to change their account details.
Swiss e-mail company held to Ransom
An e-mail company has paid ransom of over £3,600 after hacker attacks bought down their website.
The ransom was paid but the attacks continued leaving Protonmail struggling to maintain its business.
Switzerland’s national Computer Emergency Response Team which helped Protonmail through the incident advised that the attack was carried out by a cybercrime group known as Amanda Collective.
Carphone Warehouse customer data compromised
The UK’s data watchdog is “making inquiries” after Carphone Warehouse said the personal details of up to 2.4 million of its customers may have been accessed in a cyber-attack.
The encrypted credit card details of up to 90,000 people may have been accessed, the mobile phone firm said.
The Information Commissioner’s Office, which examines data breaches, confirmed it was aware of the incident.
Carphone Warehouse says the data could include names, addresses, dates of birth and bank details and it is contacting all those affected.
July 2015
A group calling itself “The Impact Team” stole the user data of Ashley Madison, a commercial website billed as enabling extramarital affairs. The group copied personal information about the site’s user base, and threatened to release users’ names and personally identifying information if Ashley Madison was not immediately shut down. In the middle of August, the group leaked more than 25 gigabytes of company data, including user details.
Because of the site’s policy of not deleting users’ personal information – including real names, home addresses, search history and credit card transaction records – many users feared being publicly shamed.
Class action litigation is now taking place with more than a dozen lawsuits being filed. It will be interesting to see how privacy courts react to this , in terms of how they treat a company who has suffered a severe breach , in terms of potential damages being awarded and the size of any fines.
Clinic data breach
The 56 Dean Street clinic in Soho – one of Europe’s busiest sexual health clinics – has apologised after mistakenly revealing the names and addresses of 780 patients with HIV in an email.
Recipients of an emailed newsletter were supposed to be blind-copied, but whoever sent it mistakenly copied email addresses into the “To:” field rather than “BCC:”, with the result that every recipient could see everyone else’s names and email addresses.
This is normally sent to individuals on an individual basis but on this occassion was sent out by email to a group of email addresses.
The Information Commissioner’s Office (ICO), is investigating this incident who can issue fines of up to £500,000 for breaches of the Data Protection Act 1998 (DPA),
British Gas details leaked
The account details of as many as 2,000 customers have been leaked online,
Email addresses and passwords to login to British Gas accounts were posted on the text upload website Pastebin, but the company believes the information leak was not as a result of its systems being breached.
The leak could be the result of a phishing attack on customers and the company is investigating the cause and will be reported to the Information Commissioners Office.
Marks & Spencer’s website suspended
Marks & Spencer was forced to suspend its website for two hours after it emerged that customers could see other people’s details when they were logged in.
Customers were able to see order histories, personal addresses and a number of other details belonging to other account holders when they logged in to register their new Sparks loyalty cards. Credit card details were not among the information being exposed.
It is unknown how many people’s details were leaked.